How to Defend your Organisation from Phishing Attacks
How to Defend your Organisation Against Phishing Attacks
Phishing attacks are happening more and more. We’ve put together below all the information you need to know about phishing attacks and how to start defending your organisation against them.
What is phishing?
Phishing is when attackers attempt to trick your staff into doing the wrong thing (the bait). This might include clicking on a link in an email which will in turn download malware onto your IT network or might direct you to a dodgy website that can try to steal your credentials or data.
Phishing can take many forms though and attackers use a variety of methods, not just emails – though this seems to be the most prevalent at the moment. Attackers can also target users on text messages, on social media or by telephone.
How do phishing email attacks work?
Phishing email attacks can install malware (such as ransomware), sabotage your systems or steal intellectual property (which can include passwords) or money.
Phishing emails are being sent to organisations of all sizes and types. Sometimes it can be a mass campaign where the attacker is sending millions of emails. Some attackers are more sophisticated and the phishing email could be the first step in a targeted attack against your company – this is known as spear phishing. These attacks may also use information about your staff or company to make their message appear very realistic. A typical example might be a director supposedly asking a member of staff to pay an invoice to a phony company, or to buy gift cards and send over the serial numbers.
What can we do to stop these attacks?
One of the best ways to combat this is to set up DMARC which stops attackers from spoofing your domain and making their emails look like they come from inside your organisation.
DMARC is a great tool and more and more businesses are being encouraged to register their details with DMARC. The more that do this, the more everyone can be assured that the emails you receive asking for information or money are genuine emails from your suppliers, partners and customers.
What else can we do?
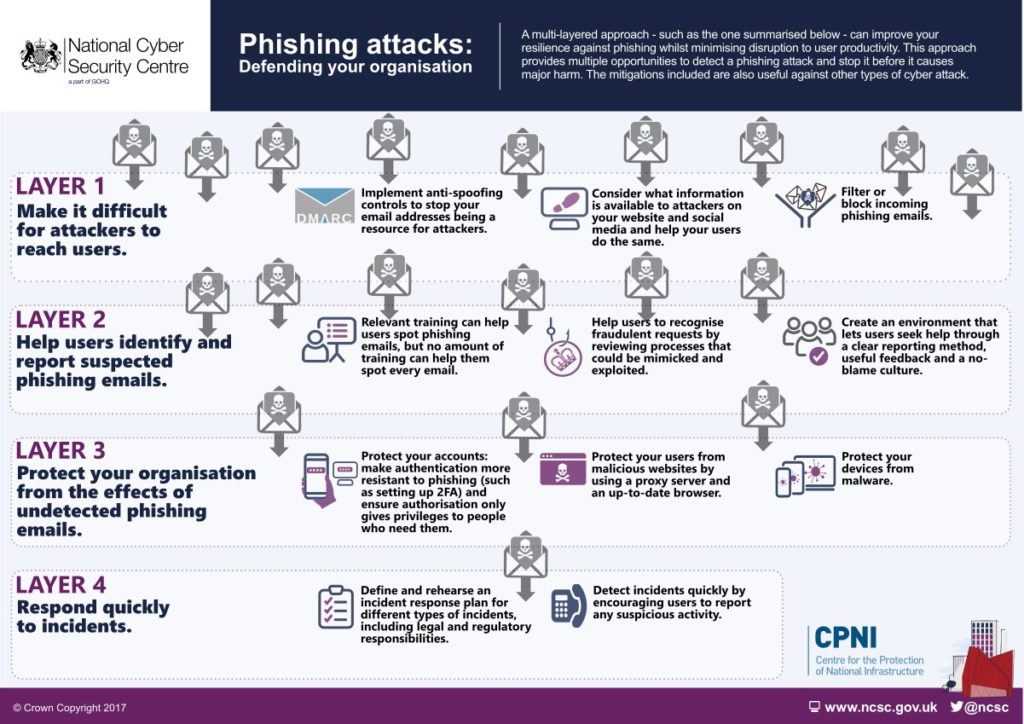
DMARC is a starting point but won’t protect your company from phishing attacks on its own. You need other systems in place, all working together, to protect your organisation.
You can do this by implementing:
- Review the information on your website – is there a lot of detail about staff which could be used in a phishing attack
- Spam filters to filter or block incoming phishing emails (easy to add to Microsoft 365)
- Phishing awareness training for all staff
- Set up Multifactor Authentication (see last week’s email for a full overview of MFA and how it is easy to set up)
- Make sure your PCs and servers are up to date with the latest software updates and security patches
Check your devices are protected. You should have anti-virus/anti-malware software on all your computers, and add MDR software to detect and stop more threats faster. MDR software from companies like Sophos and Huntress provides 24/7 threat monitoring, analysis and response from a team of experts, who can take immediate action to stop confirmed threats.
Here is a case study taken from the NCSC website which shows how phishing attacks can work and how layered defences can help protect your organisation
Case study: how multi-layered phishing mitigations defended against Dridex malware
The following real-world example illustrates how a company in the financial sector used effective layered mitigations to defend against phishing attacks.
The company, which has around 4,000 employees, received 1,800 emails containing variants of Dridex malware. The email claimed to be an invoice that needed urgent attention, which was relevant to the role of some of the recipients. It was not targeted at individual users with any personal information, but was well written, with good spelling and grammar.
If you would like to learn more about how to increase your cyber security then please give NCS IT a call – we are here to advise and help you to develop an IT strategy with cyber security at its core.
Posted in News

